Compressive Sensing
Application of Compressive Sensing for Recovering Neural Images
Neural imaging is a powerful tool in medicine, however, modern procedures are extremely costly. Our lab aims to develop techniques in order to reduce the amount of information needed in order to reconstruct an accurate medical image. There has been a plethora of research in sensor technology, but not many labs have focused on the post-imaging process. Using techniques from compressive sensing, we are developing algorithms to identify sparse neural signals with limited samples.
Pixel-Wise Exposure Control for Self-Driving Cars
Our approach : detect over/under-exposed or blurred region of the frame and adjust exposure rate of each pixel to its optimal frequency (we have the hardware patented).
Using Deep Learning to Extract Scenery Information in Real Time Spatiotemporal Compressed Sensing
Game Theory
flipIt1 or the Game of “Stealthy Takeover”
The principal motivation for the game FlipIt is the rise of Advanced Persistent Threats (APT). Advanced Persistent Threats are stealthy and constant computer hacking processes which can compro- mise security. Such threats include host takeover and compromised security keys. For host takeover, the goal of the attacker is to compromise the device while the goal of the defender is to keep the device clean through software re-installation or through other defensive precautions. Our goal is to find and implement a cost effective schedule. In other words, how often should the defender clean the machines and when should the attacker launch its next attack. For compromised security keys, the problem can similarly be formulated as finding a cost effective schedule.
These applications can be modelled by the two-player game FlipIt, in which players, attackers and defenders, vie for control of a shared resource that both players wish to control. The resource could be a computing device or a password for example, depending on which APT is being modelled. Good FlipIt strategies will help each player implement there optimal cost-effective schedule. In the first section, we present a description of the game as well as the framework, and in the second section we discuss the different agent strategies implemented as well as present some preliminary results. The last section is an overview of the future work we would like to explore. Our primary goal in this project is to find the best strategies for different variants of the game FlipIt.
These applications can be modelled by the two-player game FlipIt, in which players, attackers and defenders, vie for control of a shared resource that both players wish to control. The resource could be a computing device or a password for example, depending on which APT is being modelled. Good FlipIt strategies will help each player implement there optimal cost-effective schedule. In the first section, we present a description of the game as well as the framework, and in the second section we discuss the different agent strategies implemented as well as present some preliminary results. The last section is an overview of the future work we would like to explore. Our primary goal in this project is to find the best strategies for different variants of the game FlipIt.
1 van Dijk, M., Juels, A., Oprea, A., Rivest, R.L. FlipIt : The Game of “Stealthy Takeover”. Journal of Cryptology 26,655-713 (2013).
Using Learning to improve upon Parrondo’s Paradox
Parrondo's Paradox states that playing a combination of two losing games can lead to an overall profit. Given two games with incomplete information (i.e. the rules are not known), we developed a supervised learning framework that uses playing history to create a net winning strategy.
Graph Theory
Information Propagation in Multilayer Networks
With the emergence of social media, information and influence propagation in online networks has become an active field of research over the last decade. Individuals often participate in multiple social networks which leads to information spreading faster and the propagation becoming more complex. We would like to understand the pattern of such propagation in multilayer networks using game theoretic tools.
Machine Learning
Predicting Processor Instructions from Externally Measured EM Waves
Electromagnetic wave signals are measured externally a distance from the processor. Our goal is to classify the data for these measurements according to what process is running on the chip during measurement. We use deep learning techniques, including multilayer, recurrent, and time convolution networks.
Predicting Stock Price by Deep Neural Networks
Goal : Binary prediction, either the close price of certain stock is going higher or lower. Training Data collected from S&P500 index (20 years, 396 IT companies' daily close price). Neural network used : 1D CNN.
- CNN shows the best performance when compared with LSTM, GRU and combined
- Using Keras on top Of TenserFlow
- Loss Function : mean_squared_error(MSE)
Programming Language Correction Using RNN
A sequence to sequence learning framework that tries to make automatic corrections for code. Various structures and extensions on encoder-decoder RNNs have been applied and experimented. The figure represents a token-based encoder-decoder RNN.
Proto-object Image Saliency in Bidirectional Recurrent Neural Network
Researchers have developed many visual saliency models in order to advance the technology in computer vision.
Convolutional Neural Networks have successfully differentiated objects in images through feature extraction.
Meanwhile, Cummings et al. have proposed a proto-object based model that shows perceptual objects or shapes can be modelled through the bottom-up attention algorithm.
Inspired from their work, a Bidirectional Recurrent Neural Network is proposed for this saliency model as a machine learning alternative to capture the imbedding features in the proto-object representations.
Ransomware Detection using RNN
Our lab aims to apply machine learning on ransomware detection. Ransomware is a type of malicious software. It asks for money by threatening to publish the victim's data or perpetually block access. Recurrent neural network (RNN) is a class of artificial neural network that could make use of sequential information.
- Compared with traditional anti-virus software, this method will be quicker, smarter and more up-to-date.
- The data for training RNN is generated by collecting the behaviors of ransomware in the virtual computer.
- After training, the RNN will be sent to PCs, so that these PCs will be able to detect ransomware by using RNN to analysis the behaviors of software.
- Until now, 72% accuracy is reached.
Repair with Generative Adversarial Networks
- Want to train a deep network for repair (such as on code or text)
- Often times it is difficult to find paired (bad -> good) data on which to train
- Solution: Use A Generative Adversarial Network (GAN)
- Discriminator : whose job it is to tell real (good) samples from generated ones
- Generator : whose job it is to fool the discriminator
Seq2Tree : Dynamically Expanding Tree-Structured Neural Network
Features :
Usage :
- Self expandable at every input
- Nodes in the same subtree and on the same level follow chain dependency
- Update ancestor nodes with attention model
Usage :
- Classification model if top-level nodes are summarized to one root node
- Mask prediction if acquire one output at each node
- Generative model if additional input given to each node
Spatial and Temporal Convolutions for Event Prediction
Crime frequency varies regularly across time and space.
- Hour-to-hour quite unpredictable
- Deep Learning can handle these dependencies
- Convolutions pick up patterns across time
Tree to Tree
Sequence to Sequence (seq2seq) methods are great at translating one sequence to another. But what to do when the input structure is not a sequence? The solution is to use Tree to Tree.
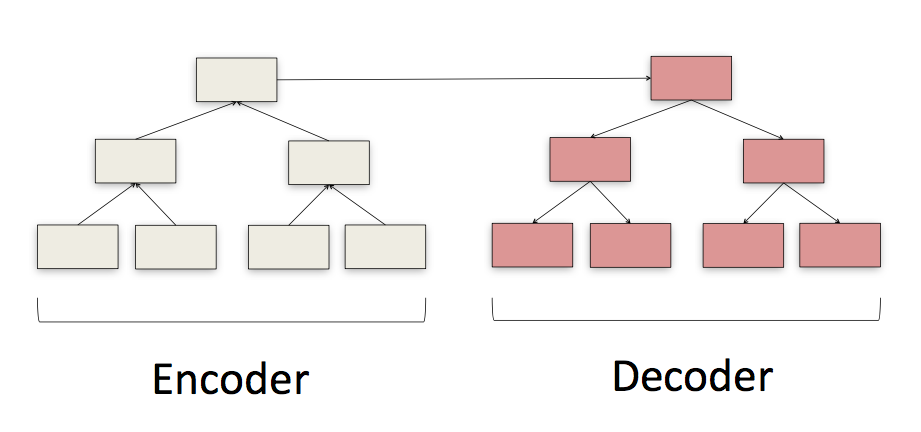

- Encoder network traverses tree from leaf to root and encodes information along the way.
- Decoder network uses this information to generate a new Tree
- Semantic information inside of non-leaf nodes is preserved yielding a more informative feature set then seq2seq
